The Centre for Chaos and Complex Networks
at the City University of Hong Kong and the Department of Electronic and
Information Engineering at the Hong Kong Polytechnic University continue their
joint seminar series in this semester, to present tutorial overviews and
original research work in the general areas of systems theory, control, complex
networks and their engineering applications.
The Jointly Seminar named “Attacks and Defenses on Machine Learning
Services” was held in PolyU on 1st Nov 2019. Mr. Huadi Zheng (PhD candidate, PolyU) was
the speaker in this seminar.
Mr. Zheng briefed the outline of his talk
included “Machine Learning (ML) Services”, “Common Attacks and Defenses”, “Model
Extraction” and “Boundary Differentially Private Layer”. Firstly, he briefed the existing popular public
prediction API such as Amazon, Google, etc.
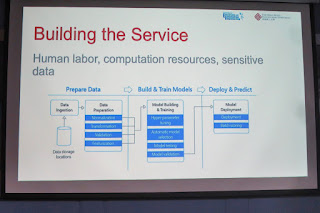
The ML service process integrated human
labor, computation resource and sensitive data.
Therefore, security and privacy were very important including training data
manipulation, model memorized data, misclassification and well-trained model to
be stolen, etc.
Then Mr. Zheng introduced Model Poisoning that
5% poisoning could cause 20% error. So that
we needed to defense through Sanctification.
He raised an example of Model Evasion that adding a noise pattern into
the image and changed the classification result. One of solutions was Adversarial Training as
defence to train the classifier with “bad” panda image.
After that he introduced the Taxonomy of ML services. Boundary Sensitive Zone (BSZ) was used to protect the privacy based on the wide of boundary that had tradeoff with accuracy.
There were two differential privacy
approach and they were Centralized Different Privacy (CDP) and Local Differential
Privacy (LDP).
Perturbation Mechanism was introduced that
the positive result had probability to be negative in next observation. Finally, Mr. Zheng summarized popular attacks
and defenses on machine learning were mentioned. A boundary differentially private layer was introduced against model extraction attacks. Lastly, he would continue to research for
handing vulnerability and counter measures.
Reference:
Centre for Chaos and Complex Networks,
CityU - http://www.ee.cityu.edu.hk/~cccn/
Department of Electronic and Information
Engineering, PolyU - http://www.eie.polyu.edu.hk/home/index.html






沒有留言:
發佈留言