Hong Kong Accreditation Service
(HKAS) and Hong Kong Council for Testing and Certification (HKCTC) co-organized
a Seminar on Cybersecurity Testing on 12 July 2018. With the rapid development
and wider use of new technology applications, such as online services, mobile
payment, cloud services and smart products, the transmission of digital data
has become frequent. This has also resulted in increasing public concern about
associated information security risks. This seminar aimed to introduce the
standards developed to address protection of smart products and IT systems from
security threats and cyber-attacks.
All guest speakers took a group
photo.
The first speaker was Mr. Ronald
Pong (Council member, Smart City Consortium) and his topic named “How to apply
ISO/IEC 15408 in Smart City for IoT Security Risk Mitigation?” Firstly, he
shared smart city smart criminal that many security issues came from IoT
devices.
Then Mr. Ronald Pong shared many security incidents including CCTV, smart car, IoT sensors, smart toys, etc. He asked us some questions including IP devices, security assurance and other awareness problem. It could raise our alert on information security around us.
After that he proposed three
level mechanism to solve the problem and they were Testing and Evaluation,
Identity and Traceability, as well as, Monitoring and Investigation.
Finally, Mr. Pong pointed out
some existing security mechanism below.
-
To use ISO 15408 Common Criteria (Evaluated Assurance Level) for all IoT
device.
-
To use ISO 26262 Road Vehicles Functional safety of electrical systems
for all Smart Car security evaluation.
-
Digital Identification (Digital Certificate) within your jurisdictions.
-
To deploy the ISO 27001 and Security Information and Event Management
(SIEM) system for IoT device.
-
To deploy ISO 17025 Computer Forensics Lab and Cross Jurisdictions
Region Digital Evidence Exchange.
For ISO 15408, he demonstrated
which countries employed for our reference.
Mr. Bernard Kan (Senior
Consultant, HKCERT, HKPC) was the second speaker and his presentation was “The
Needs of IoT Security Assessment”. In
the beginning, Mr. Kan briefed the history of the Hong Kong Computer Emergency
Response Team Coordination Centre (HKCERT) which established in 2001 and
operated by HKPC.
Mr. Bernard Kan mentioned the
potential trends in 2018 below:
1.
Financially Motivated Cyber Crimes continue to proliferate.
2.
Internet of Things (IoT) attacks on the Rise.
3.
Mobile Payment Apps as New Attack Targets
4.
More Regulation for Security and Privacy.
5.
Supply Chain Attacks bypass Enterprise Defense.
And he described how many things
connected to the internet from 2003 to 2020 (upto 50 billion!).
Mr. Kan used the following
diagram to explain what if IoTs were infected by ransomwares and it would be
terrible. He also mentioned Mirai Botnet
which was a piece of malware designed to launch multiple types of DDoS attacks
(using CCTV system and routers).
Then Mr. Kan said there was poor
or non-existent security built into the IoT device which directly exposed to
the Internet with poor network segmentation that’s why IoT Devices were so
vulnerable. He explained a simplified
IoT architecture to explain it.
Finally, Mr. Bernard Kan
concluded that need for a framework and systematic approach of assessing IoT
devices before launching in the market such as OWASP
IoT Project (Open community organization focused on improving security of
software) and shared some principles of IoT Security.
The third speaker was Mr. Hongsong
Shi (China Information Technology Security Evaluation Center) and his topic entitled
“Development and Application of the Common Criteria for IT Security Evaluation”.
Firstly, Mr. Shi explained the
interface and side channel could be the entry points of the attacks. Availability of interfaces and the existence
of weakness would induce attack. Weakness
in IT products included Design defects, Implementation errors, Delivery
loopholes, Setup mis-configuration and Environment protect inappropriateness.
Then Mr. Shi briefed the role of
security evaluation and demonstrated the general framework for security
evaluation as follow diagram.
After that Mr. Shi introduced the
history of Common Criteria (CC) which is a fundamental standard for security
evaluation using ISO/IEC 15408:2009.
Part I – The general model for
security evaluation
Part II – Security functional
components can be chosen to express requirement in a standard way (11 security
functional classes)
Part III – Security assurance
components can be used to express evaluation requirement in a generic way (7
security assurance classes & 7 predefined assurance package)
ISO/IEC 18045:2009 is a companion
standard.
The general model of Common
Criteria (CC) evaluation was showed in the following diagram. It included
Protection Profile (PP) construction, Security Target (ST) construction, Target
to Evaluation (TOE) evaluation and Certification. Moreover, 7 Predefined Evaluation Assurance
Levels (EALs) were showed as follows:
EAL 7 – Formally verified design
and tested
EAL 6 – Semi-formally verified
design and tested
EAL 5 –Semi-formally design and
tested
EAL 4 – Methodically designed,
tested and reviewed
EAL 3 – Methodically tested and
checked
EAL 2 – Structurally tested
EAL 1 – Functionally tested
At the end, Mr. Shi introduced CC
applications in China and quoted CCRA document statement as conclusion that
“The complexity of information system is such that even the most carefully
written security evaluation criteria and evaluation methodology cannot cover
every eventuality.”
The fourth speaker was Mr. Junshu
Wang (Testing Engineer, The Fifth Electronics Research Institute of the
Ministry of Industry and Information Technology) and his presentation topic was
“Introduction of ISO/IEC 15408 and its application in China”.
Mr. Wang introduced ISO/IEC 15408
structure and its target reader included consumer, developers and
evaluators. Some key words were
described as follows:
Target of evaluation (TOE): An IT
product or system and its associated guidance documentation that is the subject
of an evaluation.
Protection Profile (PP): an
implementation-independent set of security requirements for a category of TOEs
that meet specific consumer needs.
Security Target (ST): a set of
security requirements and specifications to be used as the basis for evaluation
of an identified TOE.
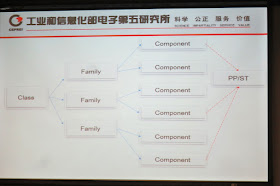
Class: a grouping of families
that share a common focus.
Component: the smallest
selectable set of elements that may be included in a PP or an ST.
The second part requirements were
discussed.
The third part had 10 classes in
security assurance requirements were also discussed.
The workflow of ISO/IEC 15408 in
China was introduced. The classified
protection of information system included “Physical Environment”, “Network
Security”, “Management System”, “Application Security” and “Host Security”.
Finally, Mr. Wang discussed a
case using ISO/IEC 15408 + PP in web application firewall using GB/T 18336
(ISO/IEC 15408) and GB/T 20281 Information security technology – Security
technical requirements and testing and evaluation approaches for firewall.
The fifth speaker was Ms. Gonda
Lamberink (Senior Business Development Manager, UL International Ltd.) and her
topic was “Tackling Insecurity of Things with UL 2900”. Firstly, she briefed the background of UL such
as UL software was used by more than 10,000 organizations in over 10
industries. Then she briefed the
insecurity of things through many security incidents.
And then Ms. Lamberink mentioned
IoT security was a commercial problem.
She introduced cybersecurity assurance program through UL 2900 series of
standards which were accreditated ANSI standards included UL 2900-1 (Software
Cybersecurity), UL 2900-2-1 (Medical Devices), UL 2900-2-2 (Industrial Control
System) and UL 2900-2-3 (Life Safety & Security).
Finally, she briefed the UL
recommended minimum security requirements and concluded TRUST was the solution
for this complexity of IoT security.
Mr. Jon Murthy (Chairs of the International Laboratory Accreditation Cooperation (ILAC) and International Accreditation Forum (IAF) Communications Committees) was the last speaker and his topic named “Cybersecurity – UK / European Experience”. Firstly, he briefed cyber crime and risk from data theft, corporate hacking, smart cities/homes and IoT, as well as transport system, etc.
Then Mr. Jon Murthy mentioned the
current situations that multiple standards and different national regulatory
responses to the market needs. For instance, industrial automation system had
many components in confined physical areas and railway system also had many
components which spread over a large physical area.
After that Mr. Murthy stated UK
experience that they had 59 laboratories accredited for IT security testing and
3,367 companies certified ISO 27001.
National Cyber Security Centre (NCSC) operated its own accredited
certification programme with 5 Accreditation Bodies and 170 Certification
Bodies.
For European experience, they recognized
the value of accreditation certification schemes on security of systems and
digital technologies. The EU is
reforming ENISA to increase the trust and security of ICT products and
services, to harmonize the existing certification landscape and to progress the
Digital Single Market. Recently, NIS Directive, GDPR and the eIDAS regulation
were driven. New ENISA Reg would require
that organizations certifying EU cyber security schemes must be accredited by the
national accreditation body in line with the requirements of regulation
765/2008.
Lastly, Mr. Murthy introduced
UNECE and IEC proposal applying in a systems-approach for the best
cybersecurity (world’s best practices through international standards) and
showed in the following diagram.
The 5 steps for this system approach
was described. The next steps were to validate
the Generic Matrix Model (GMM) approach, to obtain sector-specific GMM such as critical
infrastructure, railways, cloud computing, smart energy, smart factory and smart
building; as well as to develop risk analysis and ranking methods.
Reference:
HKCTC Seminar presentation file -
http://www.hkctc.gov.hk/en/work_seminars.html#b44
20150619: HKCTC & HKAS
Workshop on ISO 27001 ISMS Certification - https://qualityalchemist.blogspot.com/2015/06/hkctc-hkas-workshop-on-iso-27001-isms.html
20150424: PMI Seminar on QMS
based Information Security Management - http://qualityalchemist.blogspot.hk/2015/04/pmi-seminar-on-qms-based-information.html
20120214: Seminar on Supplement
VIII to CEPA for Testing and Certification Industry - https://qualityalchemist.blogspot.com/2012/02/seminar-on-supplement-viii-to-cepa-for.html
20121129: Hong Kong IT Security
Summit 2012 - https://qualityalchemist.blogspot.com/2012/11/hong-kong-it-security-summit-2012.html
20120620: Meeting with Prof.
Edward Humphreys (Father of ISMS Standard) - https://qualityalchemist.blogspot.com/2012/06/meeting-with-prof-edward-humphreys.html
20110121: Seminar on Data Privacy
- https://qualityalchemist.blogspot.com/2011/01/seminar-on-data-privacy.html
20090827: Challenges on
Information Security - https://qualityalchemist.blogspot.com/2009/08/challenges-of-information-security.html
20080802: Seminar on ISO
9001:2000 UPGRADE to 2008 Version & Secure your information with ISO 27001
- https://qualityalchemist.blogspot.com/2008/08/seminar-on-iso-90012000-upgrade-to-2008.html
Publications:
Lai, Lotto K.H. and K.S. Chin
(2014) “Development of a Failure Mode and Effects Analysis Based Risk
Assessment Tool for Information Security”,
Industrial Engineering &
Management Systems, Vol 13, No.
1, pp.88-101.
Lai, Lotto K.H., Chin, K.S. & Tsang, A.H.C. (2010) “Risk
Management of Information Security – Information Security FMEA Circle” The eighth ANQ Congress, paper HK01. (Reprinted in SQI Yearbook 2011,
pp.66-72)
Lai, Lotto K.H., Chin, K.S. & Tsang, A.H.C. (2009) “Integration
of Quality Management System and Information Security Management System – HKSTP
implementation case” Proceedings CD-ROM
of The seventh ANQ Congress, paper HK02.































沒有留言:
發佈留言